The Zero-Day Reality
Zero-day threats are no longer edge cases. They are now the preferred weapon of modern attackers.
According to OPSWAT analysis, malware complexity increased by 127 percent in the past year, and one in fourteen files initially categorized as safe by reputation sources was later proven malicious. These threats are engineered to evade static scanning, delay execution, fingerprint sandboxes, and blend into legitimate workflows.
At the same time, organizations face an impossible trade-off:
- Slow file flow to gain deeper inspection
- Or maintain speed and accept blind spots
Executables, patch files, scripts, archives, and regulated documents often cannot be sanitized or altered. That leaves a growing security gap where traditional tools fail.
MetaDefender Aether was built to close that gap.
This blog is an in-depth follow-up to the MetaDefender Aether launch announcement. It explains why unified zero-day detection at the perimeter matters, how MetaDefender Aether addresses the entire Pyramid of Pain, and how OPSWAT delivers this capability through four tightly integrated products, each designed for a specific operational reality, but all powered by the same four-layer detection pipeline.
Watch the MetaDefender Aether Overview video below to quickly gain a deeper understanding:
This short video introduces the core challenges MetaDefender Aether solves and how it stops zero-day and evasive threats before they enter the environment, without slowing file flow or overwhelming SOC teams.
Why Zero-Day Detection Must Move to the Perimeter
The perimeter is the only place where every file passes.
Email attachments, software updates, supply chain artifacts, removable media, file transfers, cloud uploads, and cross-domain exchanges all converge before files reach users or systems. Once a malicious file executes internally, response costs multiply.
However, traditional defenses were built to detect what is already known. Zero-day attacks, by definition, exploit what defenders don’t yet recognize—new malware families, modified loaders, living-off-the-land techniques, and infrastructure that rotates faster than reputation feeds can update.
At the same time, organizations are seeing:
- Explosive growth in file-based attack vectors (documents, installers, scripts, archives)
- Regulatory pressure requiring dynamic malware analysis
- SOC fatigue caused by too many tools and inconsistent verdicts
- Cloud, hybrid, and air-gapped environments that can’t rely on a single deployment model
This is the foundation of OPSWAT’s Zero-Day Detection solution.
The Only Solution to Address the Full Pyramid of Pain
Most security tools operate at the bottom of the Pyramid of Pain—hashes, IPs, and domains. These are easy for attackers to change and cheap to replace.
MetaDefender Aether is different. It is designed to apply progressive pressure across every level of the pyramid, forcing attackers to continuously re-engineer their operations.
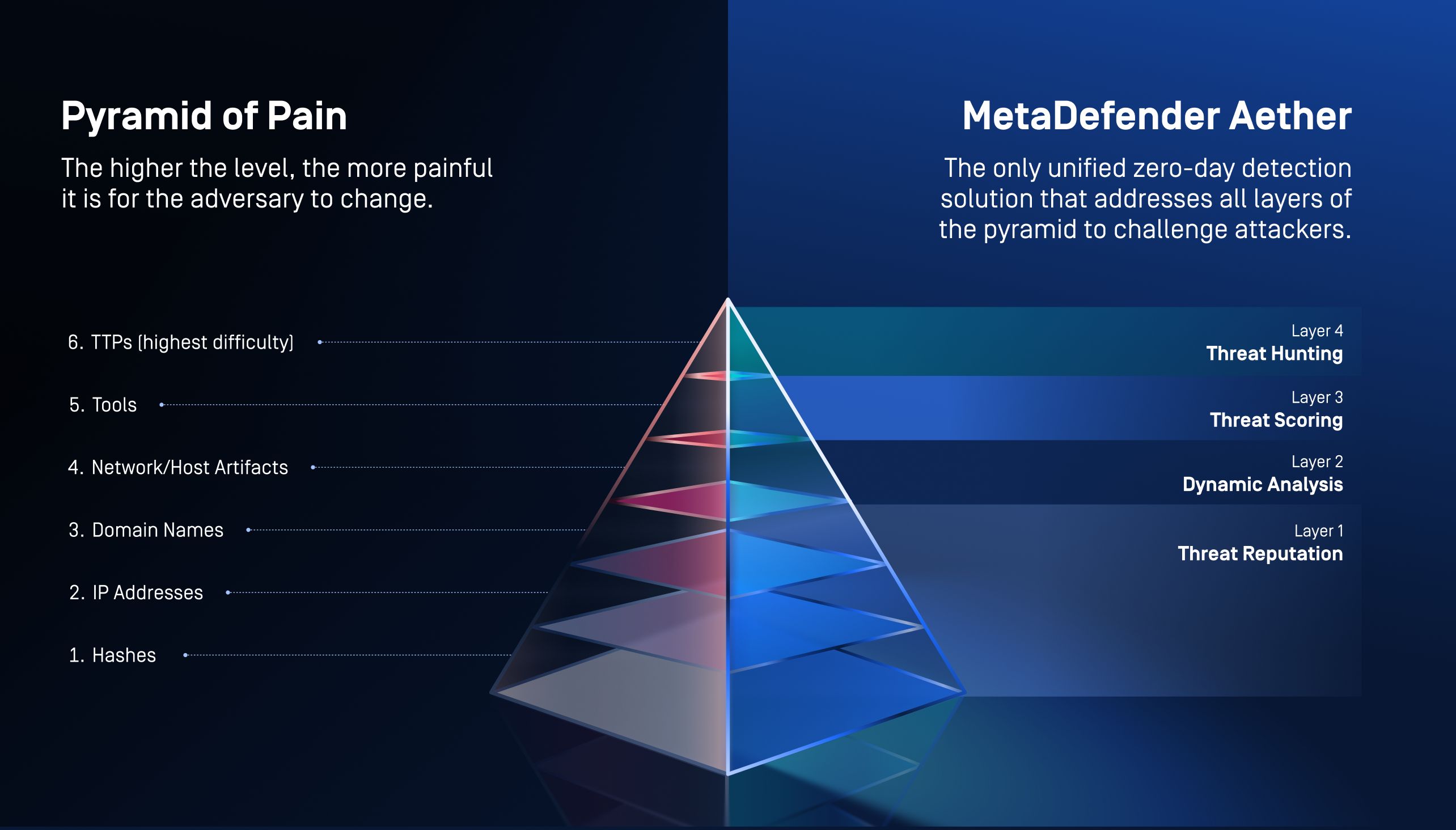
Mapping MetaDefender Aether to the Pyramid of Pain
| Targets | Kết quả | |
|---|---|---|
Lớp 1 Danh tiếng mối đe dọa | Hashes, IPs, Domains MetaDefender Aether begins with real-time and offline threat reputation checks. This layer blocks known malware, phishing infrastructure, and reused indicators instantly. |
|
Lớp 2 Dynamic Analysis [Emulation] | Artifacts and Tools Unknown and suspicious files are executed in an emulation-based environment that bypasses anti-VM and timing evasion. This reveals loader chains, memory-only payloads, dropped files, registry changes, and network callbacks. |
|
Lớp 3 Điểm số đe dọa | Tools and Techniques Behavioral indicators are correlated and scored using hundreds of malicious signals aligned with MITRE ATT&CK. This prioritizes real risk and reduces analyst noise. |
|
Lớp 4 Threat Hunting [Similarity Search] | TTPs Machine-learning similarity search correlates variants, families, and infrastructure across samples. Even when artifacts change, campaigns are exposed. |
|
Together, these layers make MetaDefender Aether the only unified zero-day detection solution designed to address the entire Pyramid of Pain.
The combined result: Aether maximizes attacker cost by addressing the entire Pyramid of Pain.
What Makes MetaDefender Aether Different
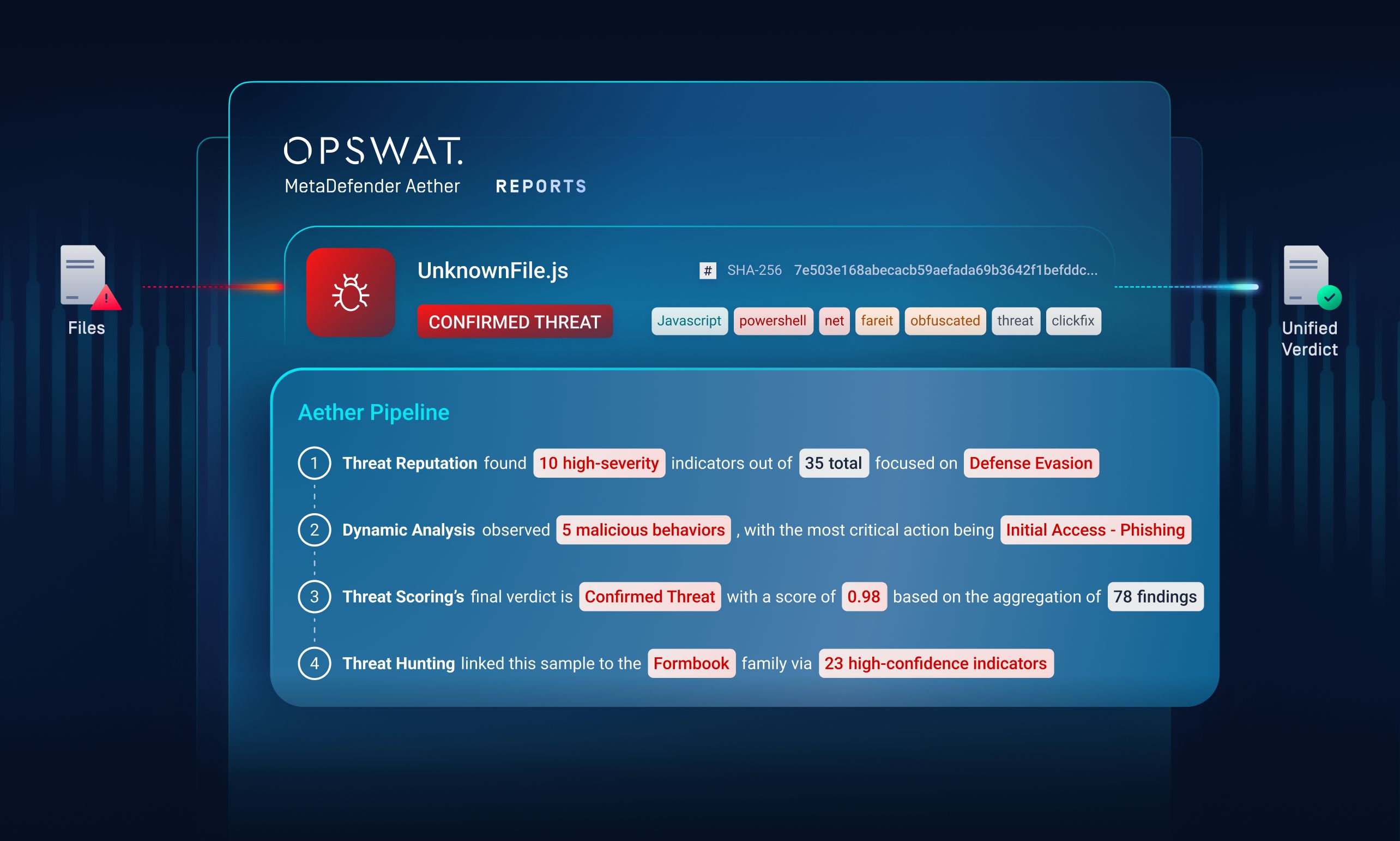
MetaDefender Aether is OPSWAT’s unified zero-day detection solution, combining four detection layers into a single, self-learning pipeline:

Layer 1 Threat Reputation
Question answered: Is the file known to be malicious?
Threat Reputation checks files, URLs, IPs, and domains against continuously updated global intelligence to instantly identify known threats. This layer stops commodity malware and phishing early, forcing attackers to constantly rotate infrastructure and reuse indicators less effectively.
Layer 2 Dynamic Analysis via Emulation
Question answered: Does the file exhibit unknown or evasive behavior?
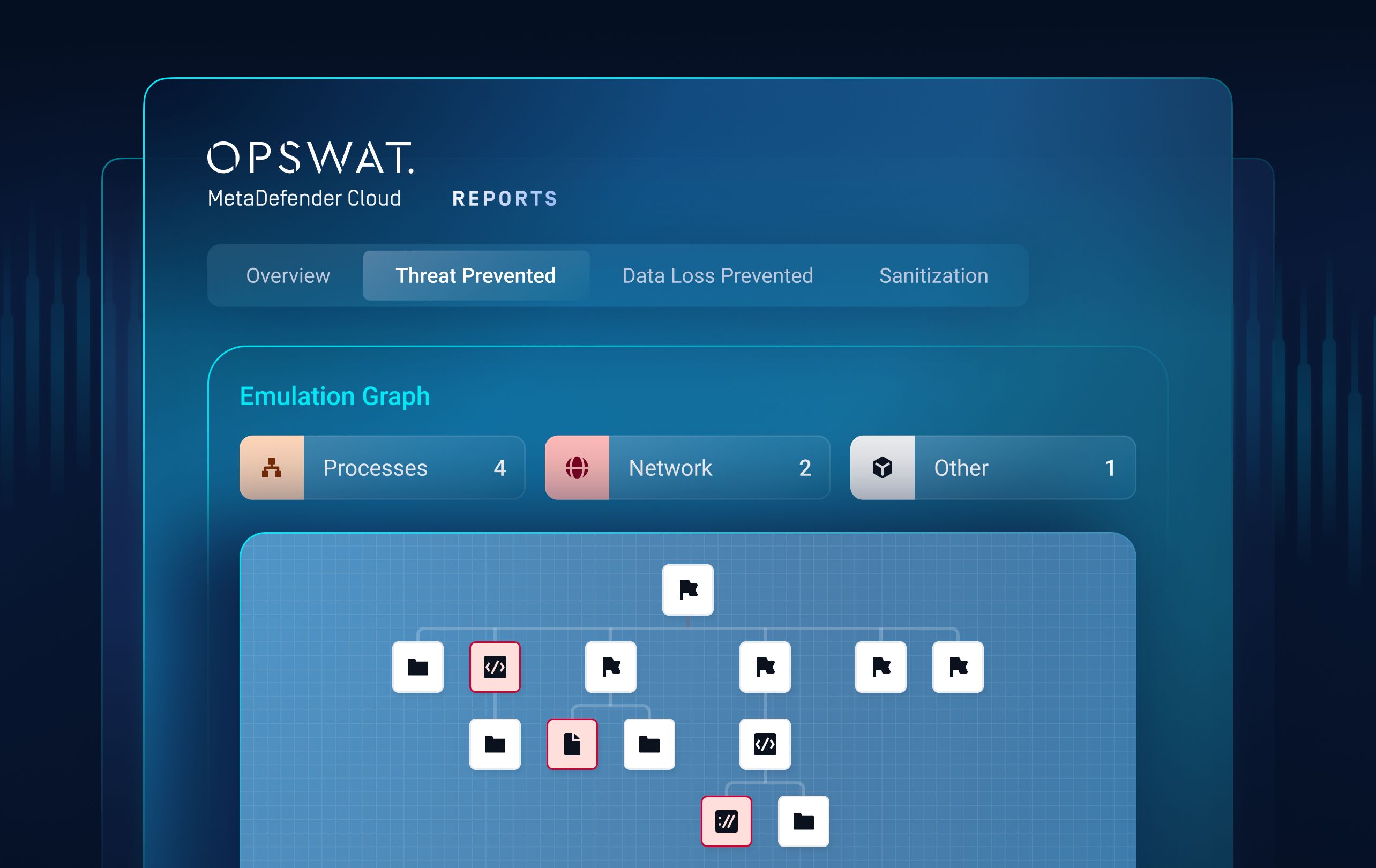
Dynamic Analysis executes suspicious files in an emulation-based environment that bypasses sandbox evasion and timing tricks. It exposes hidden behaviors such as loader chains, memory-only payloads, and multi-stage execution that static analysis and VM-based sandboxes often miss.
Layer 3 Threat Scoring
Question answered: What is the actual risk level of the zero-day threat?
Threat Scoring correlates behavioral indicators, reputation context, and detection signals to assign a confidence-based risk score. This prioritizes real threats, reduces alert fatigue, and enables SOC teams to focus on what requires immediate action.
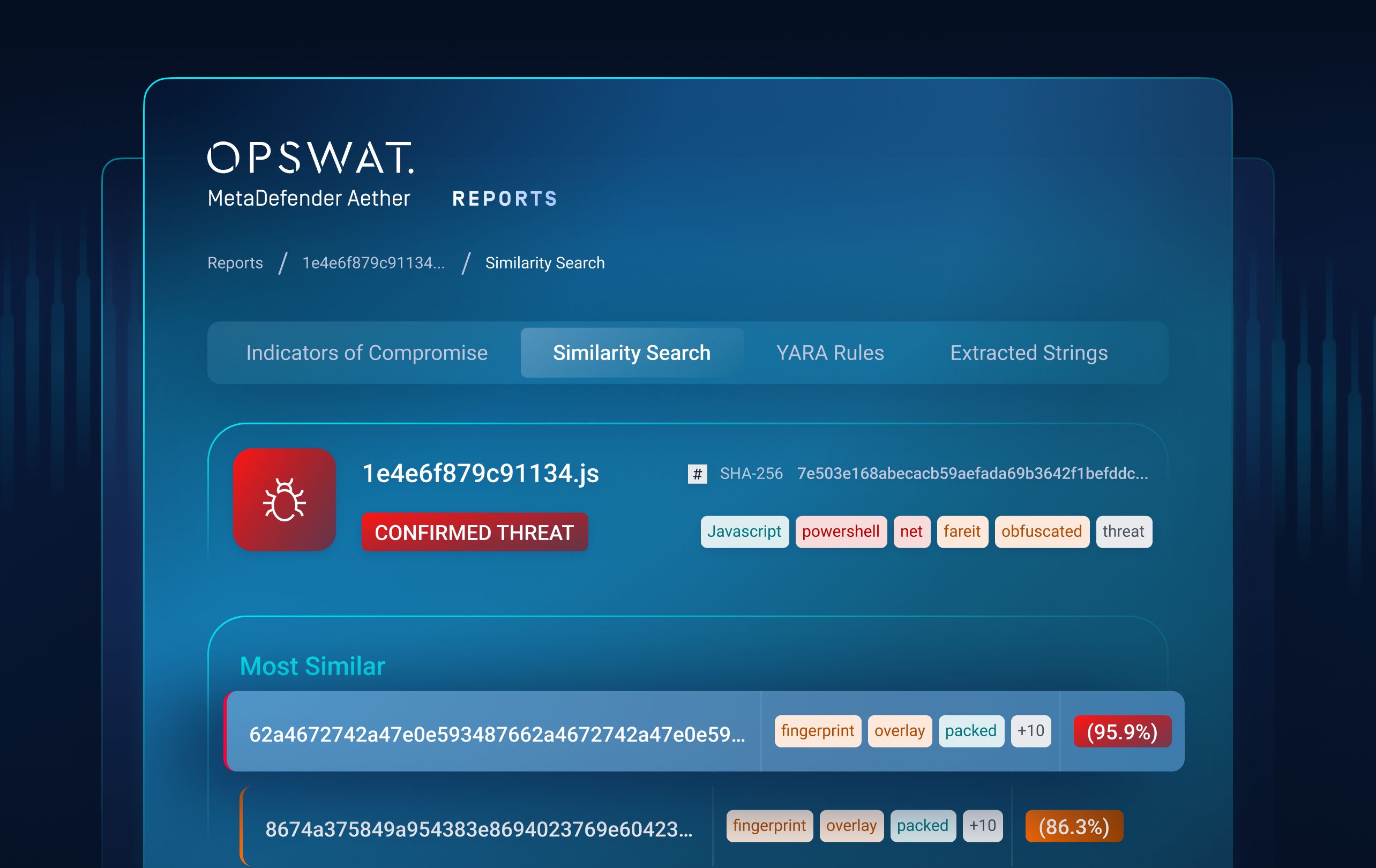
Layer 4 Threat Hunting with ML Similarity Search
Question answered: Is the zero-day threat related to broader malware campaigns?
Threat Hunting uses machine-learning similarity search to correlate unknown samples with known malware families, variants, and infrastructure. This enables campaign-level visibility and detects threats even when attackers change payloads, tools, or indicators.
Instead of multiple tools and conflicting verdicts, MetaDefender Aether delivers one trusted outcome—at scale, and at the perimeter.
The Four Products That Power Unified Zero-Day Detection
MetaDefender Aether is delivered through four tightly aligned offerings. Each solves a distinct operational challenge, while contributing intelligence back into the same detection pipeline.
MetaDefender Aether (Standalone)
For SOCs and threat hunters who need deep visibility and control
The Challenge
Security teams often rely on isolated sandboxes that are slow, VM-detectable, and disconnected from threat intelligence. Investigations require manual pivots between tools.
What Aether Delivers
- Emulation-based dynamic analysis that bypasses anti-sandbox evasion
- Threat scoring and similarity search built directly into the verdict
- Rich behavioral reporting and IOC extraction
The Transformation
Organizations gain best-in-class file verdicts, faster triage, and campaign-level insight—without sacrificing throughput.
Who Benefits
SOC analysts, malware analysts, threat hunters, and DFIR teams.
MetaDefender Aether for Cloud
For cloud-native, DevSecOps, and high-volume environments
- Learn more about MetaDefender Aether for Cloud here.
- Download the Solution Brief here.
The Challenge
Traditional sandboxes don’t scale with cloud workflows and introduce operational overhead.
What It Solves
- SaaS-based, emulation-driven detonation at cloud scale
- API-first integration with CI/CD, storage, and SaaS pipelines
- Zero infrastructure to deploy or maintain
The Transformation
Organizations maintain file velocity and volume while adding zero-day detection everywhere files move.
Who Benefits
Cloud security architects, DevSecOps teams, MSSPs, distributed SOCs.
MetaDefender Aether for Core
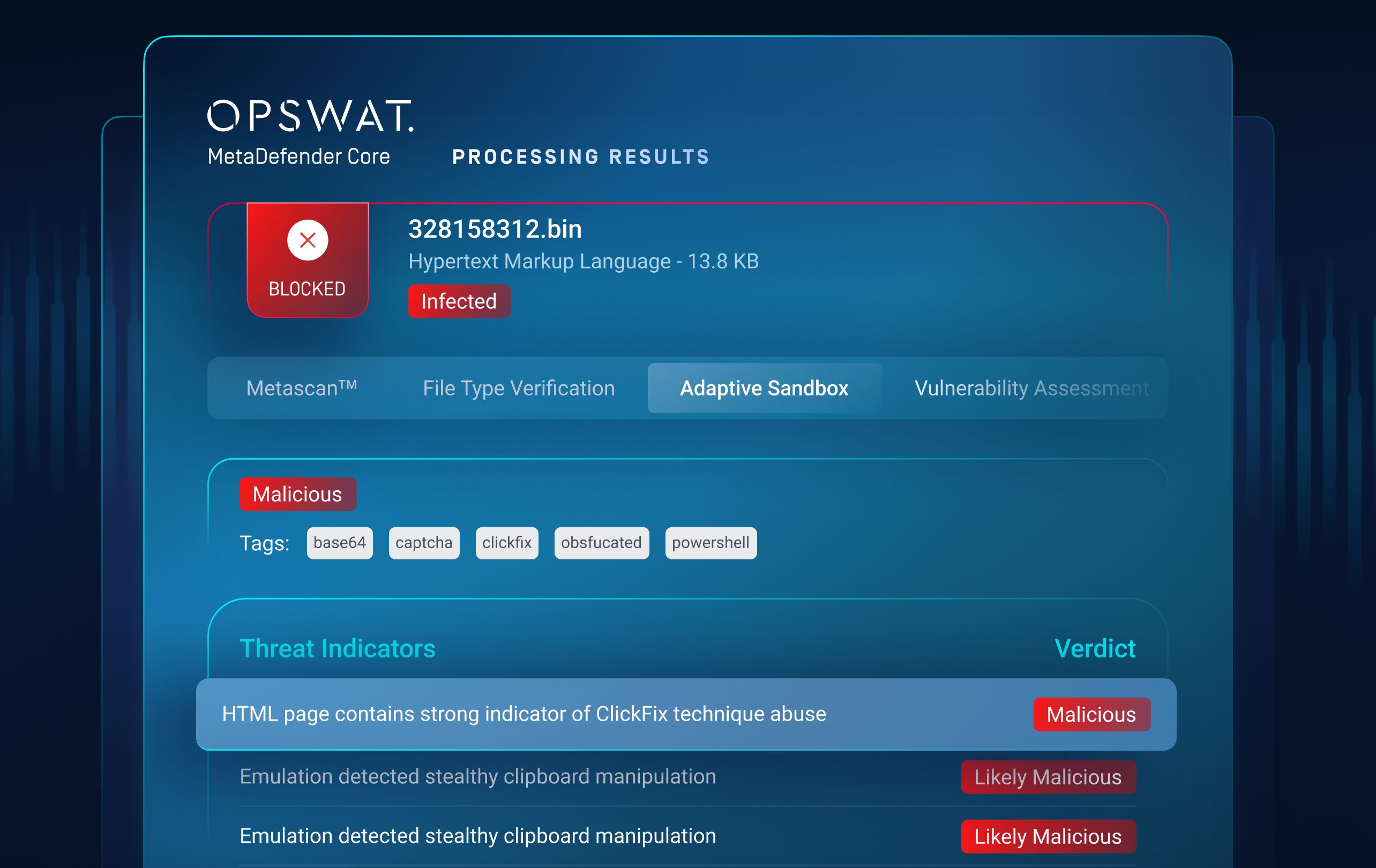
For on-premises, regulated, and air-gapped environments
- Learn more about MetaDefender Aether for Core here.
- Download the Solution Brief here.
The Challenge
Critical infrastructure and government environments cannot send files to the cloud—and still require dynamic analysis.
What It Solves
- Embedded emulation-based sandboxing inside MetaDefender Core
- Full offline operation with policy-driven workflows
- No new infrastructure required
The Transformation
Zero-day detection becomes compliant, auditable, and operationally simple—even in air-gapped networks.
Who Benefits
Security architects, OT/ICS operators, government and defense teams.
MetaDefender Threat Intelligence
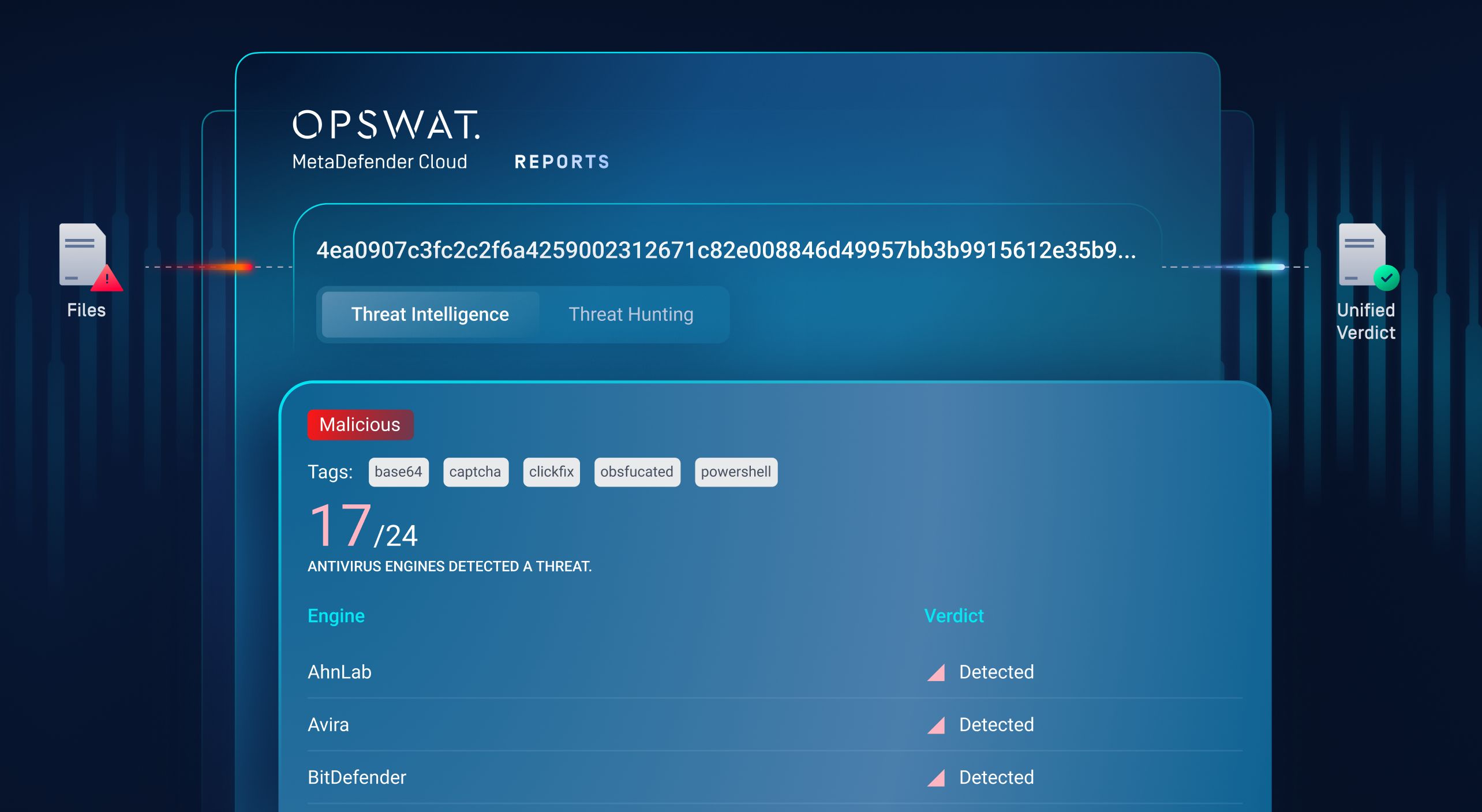
For correlation, enrichment, and proactive defense
The Challenge
Reputation-only threat intelligence lags behind modern, fast-moving attacks.
What It Solves
- Behavior-enriched IOCs from sandbox telemetry
- ML-driven similarity search to detect variants and clusters
- Seamless SIEM, SOAR, MISP, and STIX integration
The Transformation
Every unknown threat becomes actionable intelligence, strengthening future detection and reducing dwell time.
Who Benefits
Threat intelligence teams, SOCs, CISOs, platform engineers.
A New Standard for Zero-Day Defense
MetaDefender Aether represents a shift from reactive detection to proactive resilience.
Organizations that deploy Aether benefit from:
- Best-in-class file verdicts (up to 99.9% zero-day detection efficacy)
- Fast file velocity (up to 20× faster than traditional sandboxes)
- Massive file volume support at the perimeter
- Reduced SOC fatigue through a single trusted verdict
- Demonstrable compliance readiness for modern regulations
Most importantly, MetaDefender Aether changes the economics of attack by forcing adversaries to constantly rewrite their tradecraft.
Zero-day threats aren’t slowing down. Your defenses shouldn’t either.

